When it comes to crypto hardware wallets, we all get a bit anxious. Its one of those products where we are ready to spend a little extra, so our crypto assets are safe and secure. In this article lets look at the best Ledger wallet alternatives. Each of these Ledger alternatives are hand-picked based on 3 factors: Security, usability, flexibility.
SafePal
( Check Official Website )
The SafePal S1 crypto hardware wallet is backed by Binance Labs. Iis gaining popularity in the cryptocurrency community for several reasons.
Security: The SafePal S1 hardware wallet boasts a standout security feature - an EAL5+ certified secure element chip. This chip provides strong encryption and secure storage for users' private keys, helping to safeguard their digital assets against cyber threats. The EAL5+ certification is a widely recognized standard for security, adding credibility to the wallet's ability to protect users' cryptocurrency holdings. This high level of security is a significant selling point for the SafePal S1, providing users with added confidence and peace of mind when managing their digital assets.
Integrarted Dex and Binance: The SafePal S1 hardware wallet offers added convenience with its built-in decentralized exchange and integration with the Binance exchange. This enables users to easily swap or exchange cryptocurrencies within the wallet's app and engage in spot trading directly from their wallet. These features make it stand out as one of the most desired Ledger alternatives.
SafePal is priced to be very affordable despite its advanced features. The SafePal S1 costs $49.99 and the S1 Pro costs $89.99. Making it accessible to a broader range of users.
Distinctive design: The SafePal S1 hardware wallet is designed to be compact and portable, resembling a large credit card with a camera on the back. This design contributes to its ease of use and makes it a convenient option for those who value mobility. The inclusion of a camera adds to the functionality of the wallet, allowing users to easily perform actions that require visual input.
Ecosystem and support: The SafePal S1 supports a wide range of cryptocurrencies, with compatibility for 10,000+ tokens across 20 different blockchains. SafePal's strategic partnerships and participation in the Web 3.0 movement have been key to its growth in the hardware wallet market. By offering secure and convenient solutions, SafePal is contributing to the growth of the cryptocurrency ecosystem and shaping the future of cryptocurrency storage. The mobile app is easy to use and connected to a plethora of decentralized applications (dApps). Also allows users to participate in yield farming sort activities.
All these advantages collectively position the SafePal as one of the best Ledger wallet alternatives.
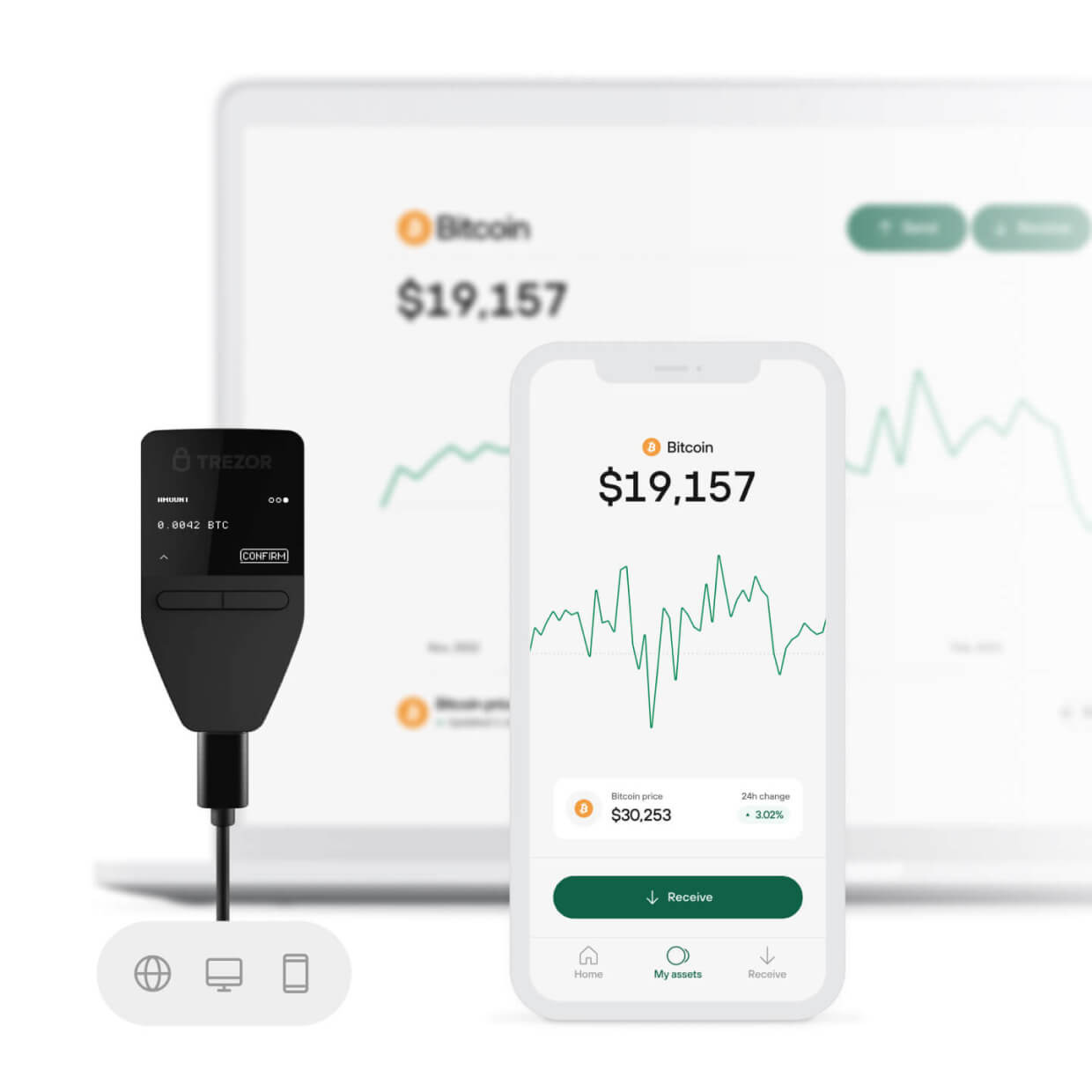
Trezor
( Check Official Website )
The Trezor Safe 3 hardware wallet ( latest offering from Trezor as of 2024 ) offers several upgrades and unique features compared to previous models and competitors. The user-friendly interface of the app and the wallet, makes it accessible for beginners in the crypto space.
Secure Element Chip: The Trezor Safe 3 includes a Secure Element chip, a first for Trezor wallets. This chip enhances the physical security of the device, particularly in protecting the PIN and verifying the authenticity of the device.
Support for Over 8,000 Crypto Assets: The Trezor Safe 3 hardware wallet offers support for a wide range of cryptocurrencies and tokens, including major cryptocurrencies, ERC-20 tokens, and NFTs. With its commitment to supporting a wide range of digital assets, the Trezor Safe 3 is a comprehensive and reliable Ledger alternative.
Like the Trezor Model T, the Safe 3 supports Shamir Backup. Its a advanced method for securing recovery seeds by splitting the recovery method across multiple keys or individuals.
To enhance privacy, the Trezor Safe 3 supports CoinJoin for Bitcoin transaction privacy and the Tor browser for anonymous communication. These features provide added security and privacy, making it a strong choice.
Integrations: The device seamlessly integrates with various 3rd party wallets like Yoroi, MyEtherWallet and Exodus.
And its affordable. At $79, the Trezor Safe 3 is one of the Ledger wallet alternatives on the market.
While the Trezor Safe 3 may not have a touchscreen or support for certain popular networks like Cosmos, it still offers a compelling set of features for those seeking a secure and user-friendly hardware wallet.
Bitkey
This wallet is a product of Block, Inc., offers a unique approach to Bitcoin self-custody. Developed by the co-founder of Twitter, Jack Dorsey.
2-of-3 Multi-Signature Wallet: The BitKey wallet utilizes a multi-signature model that requires any two of three keys to authorize transactions, adding a robust layer of security. This model utilizes a key on the user's phone, a key on the hardware device, and a third key stored on BitKey's server. This approach helps to ensure that no single point of failure can compromise the user's funds, providing enhanced protection against potential security threats. Overall, the BitKey wallet offers users a powerful tool for securing their Bitcoin holdings and participating in the world of cryptocurrency with confidence.
No Seed Phrases: BitKey offers a user-friendly alternative to the traditional seed phrase backup system used in many hardware wallets. This design choice is aimed at simplifying the user experience and making it easier for users to protect their Bitcoin holdings. This focus on user experience is a notable feature of the BitKey wallet and reflects the company's commitment to providing a high-quality solution for managing Bitcoin. Making it one of the best Ledger wallet alternatives.
Mobile and Hardware Key Integration: BitKey integrates a mobile app and a hardware device to provide users with a balance of security and convenience. The mobile app allows for easy transaction management, while the hardware device adds an extra layer of protection. The hardware key is intended for significant transactions and security adjustments, while the mobile key can be used for smaller, everyday transactions. This integration offers users a versatile solution for managing their Bitcoin securely and conveniently, with the flexibility to adapt to different needs and usage scenarios.
Server Key for Recovery: The server key integrated into the BitKey wallet is a critical component for recovering the wallet if both the phone and hardware device are lost. It also assists in signing transactions within the mobile key limits, providing added security and convenience for users. This feature helps mitigate the risks associated with cryptocurrency ownership and adds to the overall security and reliability of the BitKey platform.
Elegant Design: The wallet includes a sleek mobile app and an “Apple grade” fancy looking hardware device. Its designed to provide a more secure and user-friendly Bitcoin management experience.
Major platform integrtions: BitKey is integrated with platforms like Coinbase and Cash App. This simplifies the process of Bitcoin withdrawals and enhancing user convenience.
The BitKey wallet represents a significant step in the evolution of Bitcoin self-custody solutions, focusing on user control, security, and a simplified experience. Its one of the top Ledger alternatives to consider.
Disclaimer:
Affiliate Links Disclosure: Please be aware that this website includes product affiliate links. In the event that you make a purchase after clicking on one of these links, we may earn a commission -or- direct payment. This disclosure is made to keep you informed about our affiliate relationships and to maintain transparency. Your support is highly appreciated!
Industry update:
Digital Warfare: North Korea's $3B Crypto Heist Funds Nuclear Ambitions
Published date: 21/10/2024
Microsoft's latest Digital Defence Report has revealed that North Korean state-sponsored hackers have systematically stolen approximately $3 billion in cryptocurrency since 2017, with up to $1 billion taken in 2023 alone. These funds, according to the report, are directly financing more than half of Pyongyang's nuclear weapons program.
"The scale and sophistication of these operations represent a significant evolution in state-sponsored cyber threats," explains Thomas Chen, cybersecurity analyst at Morgan Stanley. "We're seeing traditional geopolitical tensions migrate into the digital asset space." The findings underscore the growing intersection of cryptocurrency security and national security concerns.
Microsoft's investigation has identified several new North Korean hacking groups, including Moonstone Sleet, Jade Sleet, Sapphire Sleet, and Citrine Sleet, each specializing in targeting cryptocurrency organizations. Of particular concern is Moonstone Sleet's development of custom ransomware targeting aerospace and defense sectors.
"These aren't opportunistic cybercriminals – they're state-funded operations with strategic objectives," notes Sarah Thompson, director of digital security at Goldman Sachs. The groups demonstrate increasing technical sophistication, reflecting substantial investment in resources and training.
Tom Burt, Microsoft's vice president of customer security and trust, emphasizes the escalating nature of state-sponsored cyber threats. The report indicates that nation-states, particularly Russia, China, and Iran, are becoming more aggressive in their cyber operations, especially as the U.S. presidential election approaches and geopolitical tensions persist in Europe and the Middle East.
The financial implications are substantial. "A $3 billion theft represents one of the largest state-sponsored cryptocurrency heists in history," explains Marcus Rodriguez, chief crypto analyst at Deutsche Bank. "This demonstrates how digital assets can be exploited to circumvent traditional financial sanctions."
In response to these threats, South Korea, the United States, and Japan have announced enhanced coordination to combat North Korea's illegal cyber activities. "International cooperation is crucial," says Patricia Wong, senior fellow at the Digital Security Institute. "These attacks exploit the borderless nature of cryptocurrency transactions."
The trilateral agreement emphasizes private sector partnerships, particularly with cryptocurrency service providers. "Traditional cybersecurity measures aren't sufficient against state-sponsored threats," notes James Chen, cyber defense strategist at Asia Pacific Security Alliance. "We need integrated responses that combine government intelligence with private sector innovation."
Market observers point to broader implications for the cryptocurrency industry. "These attacks highlight the critical need for enhanced security protocols in digital asset management," explains Victoria Zhang, digital asset security specialist at JP Morgan. "Institutional investors are particularly concerned about state-sponsored threats."
The financial sector is responding with increased security measures. Major cryptocurrency exchanges report implementing additional verification layers and monitoring systems specifically designed to detect state-sponsored activities. However, experts warn that the threat landscape continues to evolve rapidly.
As one senior cybersecurity executive noted: "This isn't just about protecting digital assets anymore. It's about preventing rogue states from funding weapons programs through cryptocurrency theft." The challenge now lies in developing security measures that can keep pace with increasingly sophisticated state-sponsored cyber operations.